Introduction
In merger and acquisition (M&A) scenarios, organizations often need to consolidate Microsoft Entra ID tenants while continuing to maintain separate Active Directory (AD) forests. This blog focuses solely on the identity migration process between two Microsoft 365 tenants with hybrid environments. The source and destination tenants each have their own AD forests. During the cutover, the custom domain is removed from the source tenant and added to the destination tenant. This guide walks through each step required to successfully migrate user identities while maintaining hybrid sync.
Current Setup Overview
- AD Forest: defender.local
- M365 Tenant Domain: defender4.cloud
- Hybrid Users: sunil@defender4.cloud, anil@defender4.cloud
- AD Forest: m365cloud.local
- M365 Tenant Domain: acmebh.com
Note: This blog only covers identity migration. For migrating user data such as emails, files, and Teams content, you can use Microsoft native cross-tenant tools or third-party solutions such as BitTitan, ShareGate, AvePoint, or Quest.
How to Migrate Users and Data Between Microsoft 365 Tenants
Step-1 Identity Preparation Before Data Migration
Since this migration is happening in a hybrid environment, and we’re moving data from the source Microsoft 365 tenant—including Exchange Online, SharePoint Online, OneDrive, and Teams. we must first provision user identities in the destination tenant to facilitate the data copy.However, you cannot add the source tenant’s custom domain to the destination tenant at this stage, as Microsoft enforces a restriction that a domain can be associated with only one M365 tenant at a time.
⚠️ Important Considerations:
- Avoid Username Conflicts: Before creating accounts, conduct a thorough review of user UPNs and email addresses to ensure there are no naming collisions in the destination tenant.
- Check Existing Users: If any usernames are already present under the destination tenant’s default onmicrosoft.com domain or an existing custom domain, those will block provisioning.
- Temporary Domain Strategy: If conflicts arise, consider purchasing a temporary domain for initial user provisioning and data copy. This temporary domain will serve only during the transition period.
Once the source tenant’s custom domain is fully removed, you can reassign it to the destination tenant and update user UPNs and email addresses accordingly.
In our test scenario, we’re working with only two user accounts, and there are no naming conflicts with the destination tenant. Therefore, we’ll manually create these accounts directly from the Microsoft 365 Admin Center in the destination tenant.
- Avoid Username Conflicts: Before creating accounts, conduct a thorough review of user UPNs and email addresses to ensure there are no naming collisions in the destination tenant.
- Check Existing Users: If any usernames are already present under the destination tenant’s default onmicrosoft.com domain or an existing custom domain, those will block provisioning.
- Temporary Domain Strategy: If conflicts arise, consider purchasing a temporary domain for initial user provisioning and data copy. This temporary domain will serve only during the transition period.
For larger migrations: If you're dealing with a larger number of users, it's recommended to use PowerShell scripts or bulk provisioning methods (such as CSV import) to automate user creation efficiently.
As shown in the screenshot, the user account has been successfully created in the destination tenant and licensed accordingly.
Step 2: Data Migration
Now that the user accounts have been successfully created in the destination tenant, you can begin the data migration process using your preferred migration tool.
This step involves copying content from services such as Exchange Online, OneDrive, SharePoint Online, and Teams from the source tenant to the target tenant.
Important: The domain cutover timing will vary depending on the tool used, the volume of data, and the complexity of the migration. At this stage, it’s also crucial to monitor for and resolve any data integrity issues that may arise during transfer.
- BitTitan MigrationWiz
- ShareGate
- AvePoint
- Quest Migration Manager
Each of these tools comes with its own prerequisites, features, and supported workloads. Choose the one that best fits your organization’s needs, and make sure to coordinate closely with your migration tool provider to plan this phase thoroughly.
Step 3: On-Premises AD & Entra Connect Preparation for Domain Cutover
Once the data migration is complete, you can begin planning for the domain cutover, which typically requires a full day. Before proceeding, ensure that the following prerequisites are in place to enable a smooth transition1. Source and Destination AD Forest Network Connectivity
Goal: Ensure domain controllers from both forests can communicate with each other across the network.
Once connectivity is confirmed, proceed to establish DNS name resolution between the two forests.
2. Configure DNS Conditional Forwarding
To enable seamless name resolution between the forests, configure DNS conditional forwarding on both sides. This is essential for trust creation and domain communication.
For example, in our case:
- Source Forest:
defender.local - Destination Forest:
m365cloud.local
Configure each forest’s DNS server to forward queries for the other forest’s namespace to the appropriate internal DNS IPs.
Log in to the Domain Controller in each forest, then follow these steps:
- Press
Win + Rto open the Run dialog. - Type
dnsmgmt.mscand press Enter to launch the DNS Manager. - In the DNS Manager console, expand the server node.
- Right-click on Conditional Forwarders and select New Conditional Forwarder.
Name resolution between the destination and source forests is now active
Configuring Conditional Forwarder in the Source Forest
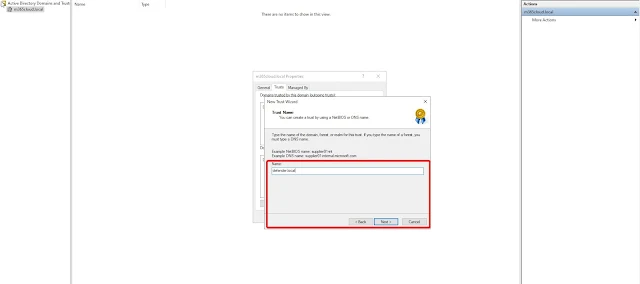
3. Forest Trust Configuration Between Source and Destination Forests
The Direction of Trust window will appear next, where you'll need to specify how authentication should flow between the two forests. In our case, we’ll select Two-way, which allows users in both forests to authenticate with resources in each other's domains, enabling full bidirectional trust. Once selected click Next
The Sides of Trust window determines where the trust relationship should be created. You have the option to configure the trust on this domain only or on both domains. While it's possible to set up the trust on one domain and then repeat the steps manually on the other forest, it's more efficient to choose Both this domain and the specified domain. This allows the trust to be established on both sides in a single workflow, provided you have the necessary credentials for the remote forest.
Since we selected the option to create the trust on both this domain and the specified domain, you will now be prompted to enter the privileged username and password for the other forest. Provide the credentials of an account with sufficient administrative rights in the remote domain, then click Next to proceed with the trust configuration.
Now, you’ll need to configure the outgoing trust authentication level for the specified (remote) forest. Similar to the previous step, we’ll choose Forest-wide authentication, which allows users from any domain within the specified forest to be authenticated in the local forest. This ensures consistent access and trust behavior across both environments .Click Next to continue
Finally, you’ll reach the Completing the New Trust Wizard screen. Review the summary, and click Finish to complete the forest trust configuration.
The forest trust is now successfully established and active in both the source and destination forests. You can verify this from the Trusts tab within the Active Directory Domains and Trusts console on each domain controller.
This trust enables secure identity recognition and resource sharing between the two environments—critical for hybrid coexistence and migration scenarios.
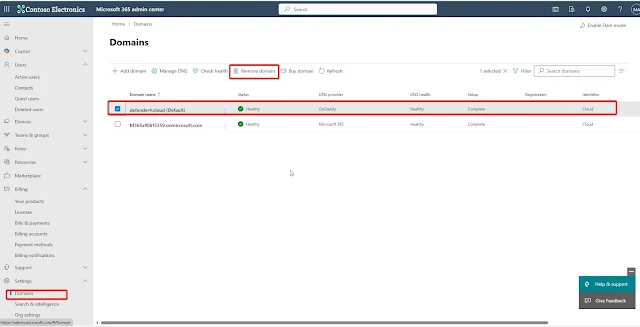
4.Domain Removal from Source Microsoft 365 Tenant
This includes updating the domain name on all users, groups, and applications that are currently using the custom domain. In our case, we only have two hybrid user accounts that need to be updated.
Since you’ll likely need to perform a final data migration to the destination tenant, it’s recommended to retain these accounts as cloud-only, using a temporary domain such as onmicrosoft.com, to avoid sync-related complications.
Uncheck the OU containing the users you want to convert.
⚠️ No additional configuration is needed. After completing the steps, the selected users will be deleted from Entra ID during the next directory sync cycle. These users can then be manually restored as cloud-only accounts.⚠️ Important: Always ensure that deleted users are successfully restored as cloud-only accounts before removing the custom domain from the tenant. If you remove user from directory sync and then immediately delete the domain, any attempt to restore users afterward may result in errors—such as Entra ID being unable to reconnect mailboxes to user accounts.
5. Destination Forest Entra Connect Setup – Connecting to Source Forest & Domain Configuration
- Go to the Microsoft 365 Admin Center in the destination tenant.
- Navigate to Settings > Domains and click Add Domain.
- Enter the domain name (e.g.,
defender4.cloud), then follow the prompts to add the TXT record to your DNS provider for domain verification. - Once the domain is verified, proceed to the next step.
What's Not Covered in This Blog
- Cleaning up Entra Hybrid Join records from source device.
- Unenrolling from Intune and re-enrolling in the destination tenant.
- Offboarding Defender for Endpoint from source and onboarding to destination.













































































4 Comments
Hello,
ReplyDeleteNext, will you be taking about what to do with the workstations? Cached credentials. Resetting workload apps.disjoining from hybrid andor going entra joined? Perhaps you want to include powersyncpro migration agent in this discussion? Have a chat with me Neil at powersyncpro dot com
Hi Neil,
ReplyDeleteThank you for your comment.
I’ve already had a discussion with Anna and conducted a demo session of PowerSyncPro a couple of months ago in response to one of our customer requirements.
Hi Sreejith,
ReplyDeletethanks for this great work. Helps a lot.
One question i have come across is, why would we have to create the users in the target tenant manually, if later AD Connect (new tenant to source AD) would create them anyway?
Thx,
Miguel
Hi Miguel,
ReplyDeleteGreat question.
Essentially, we need to copy the users’ data to the target tenant without impacting their current sign-in or overall experience. This data migration will run in the background using migration tools. In preparation, we are provisioning cloud-only accounts. Then, on the cutover day,once the domain is removed from the source tenant and added to the target, we’ll perform soft matching with AD Connect.
This scenario involves two different AD forests but focuses only on consolidating the Microsoft 365 tenants, not the AD forests themselves. If both the AD forests and Microsoft 365 tenants were being consolidated, then users could either be created directly in the target AD or migrated from the source forest with SID history.