In today's digital landscape, where security threats are ever-evolving, simply relying on default settings is rarely sufficient. As an M365 Admin, you have the critical responsibility of tailoring Microsoft Entra ID settings to secure your organization while delivering an optimized, seamless experience for end users. This blog dives into the top recommended settings to strengthen the security posture of your Microsoft Entra ID tenant beyond the defaults.
What's New in Microsoft Entra ID
Before diving into the essential security settings of Entra ID, let’s take a quick look at a valuable resource: the "What’s New" tab in the Microsoft Entra ID portal On the left side of the portal, this tab provides quick access to Entra Highlights, including top announcements, new releases, and change notifications. Additionally, under the "Roadmap" tab, you’ll find features in Public Preview and General Availability, complete with their release dates and statuses. As an M365 Admin, regularly checking the "What’s New" tab helps you stay prepared to adopt new features, leverage added benefits, and enhance your environment’s configuration.
Entra ID Recommendations
The Microsoft Entra recommendations feature helps monitor your tenant’s security and health, ensuring you get the most out of Microsoft Entra ID. These recommendations now include Identity Secure Score, which provides insights into the security of your tenant, offering a score based on various security factors.
These personalized recommendations give actionable guidance to:
- Identify opportunities to implement best practices.
- Improve your tenant’s security state.
- Optimize configurations for your scenarios.
Microsoft Entra ID analyzes your tenant daily, comparing its configuration to security best practices. Applicable recommendations are prioritized in the Recommendations section of the identity overview, helping you focus on critical areas. Each recommendation includes a description, value summary, step-by-step action plan, and impacted resources, making it easy to address security issues efficiently. The Identity Secure Score at the top of the page provides a numerical representation of your tenant's overall security health.
| Recommendation | Impacted Resources | Required License | Availability |
|---|---|---|---|
| Enable Microsoft Purview Adaptive Protection and the Insider Risk condition in Conditional Access | Users | Microsoft Entra Premium P2 | Generally Available |
| Convert per-user MFA to Conditional Access MFA | Users | All licenses | Generally Available |
| Migrate applications from AD FS to Microsoft Entra ID | Applications | All licenses | Generally Available |
| Migrate apps and service principals from Azure AD Graph to Microsoft Graph | Applications | All licenses | Public Preview |
| Migrate from ADAL to MSAL | Applications | All licenses | Generally Available |
| Migrate from MFA server to Microsoft Entra MFA | Tenant level | All licenses | Generally Available |
| Migrate to Microsoft Authenticator | Users | All licenses | Preview |
| Minimize MFA prompts from known devices | Users | All licenses | Generally Available |
| Remove unused applications | Applications | Microsoft Entra Workload ID Premium | Public Preview |
| Remove unused credentials from applications | Applications | Microsoft Entra Workload ID Premium | Public Preview |
| Renew expiring application credentials | Applications | Microsoft Entra Workload ID Premium | Public Preview |
| Renew expiring service principal credentials | Applications | Microsoft Entra Workload ID Premium | Public Preview |
| Recommendation Title | Target Roles |
|---|---|
| AAD Connect Deprecated | Hybrid Identity Administrator |
| Convert per-user MFA to Conditional Access MFA | Security Administrator |
| Designate more than one Global Administrator | Global Administrator |
| Do not allow users to grant consent to unreliable applications | Global Administrator |
| Do not expire passwords | Global Administrator |
| Enable password hash sync if hybrid | Hybrid Identity Administrator |
| Enable policy to block legacy authentication | Conditional Access Administrator, Security Administrator |
| Enable self-service password reset | Authentication Policy Administrator |
| Ensure all users can complete multifactor authentication | Conditional Access Administrator, Security Administrator |
| Long-lived credentials in applications | Global Administrator |
| Migrate Applications from the retiring Azure AD Graph APIs to Microsoft Graph | Application Administrator |
| Migrate applications from AD FS to Microsoft Entra ID | Application Administrator, Authentication Administrator, Hybrid Identity Administrator |
| Migrate authentication methods off the legacy MFA & SSPR policies | Global Administrator |
| Migrate from ADAL to MSAL | Application Administrator |
| Migrate from MFA Server to Microsoft Entra MFA | Global Administrator |
| Migrate service principals from the retiring Azure AD Graph APIs to Microsoft Graph | Application Administrator |
| MS Graph versioning | Global Administrator |
| Optimize tenant MFA | Security Administrator |
| Protect all users with a sign-in risk policy | Conditional Access Administrator, Security Administrator |
| Protect all users with a user risk policy | Conditional Access Administrator, Security Administrator |
| Protect your tenant with Insider Risk Conditional Access policy | Conditional Access Administrator, Security Administrator |
| Remove overprivileged permissions for your applications | Global Administrator |
| Remove unused applications | Application Administrator |
| Remove unused credentials from applications | Application Administrator |
| Renew expiring application credentials | Application Administrator |
| Renew expiring credentials for service principals | Application Administrator |
| Require MFA for administrative roles | Conditional Access Administrator, Security Administrator |
| Review inactive users with Access Reviews | Identity Governance Administrator |
| Secure and govern your apps with automatic user and group provisioning | Application Administrator, IT Governance Administrator |
| Use least privileged administrative roles | Privileged Role Administrator |
| Verify App Publisher | Global Administrator |
Entra ID User Settings
- By setting the Register applications option to "No," you prevent users from creating application registrations. To allow specific individuals to register applications, you can assign them the Application Developer role, giving them the necessary permissions. You can read more about Entra ID Application User and Admin consent here.
- Restrict non-admin users from creating tenants: Users can create new tenants in the Microsoft Entra portal, The creator becomes the Global Administrator of the new tenant, which doesn’t inherit any existing settings. Setting this to Yes restricts tenant creation to users with the Tenant Creator role. Setting it to No allows non-admin users to create tenants, with actions still logged .Set this to Yes and assign the Tenant Creator role to specific non-admin users to allow them to create new tenants.
- Create security groups: Setting this option to No prevents users from creating security groups. However, users with the User Administrator role or higher will still retain the ability to create security groups.
- Guest user access restrictions: Setting the Guest user access option to Guest user access is restricted to properties and memberships of their own directory objects limits guest users to viewing only their own profile information. By default, they cannot access other users’ information, even when searching by user principal name, object ID, or display name. Additionally, guest users are restricted from viewing group information, including group memberships.
However, this setting does not prevent access to groups they are part of in certain Microsoft 365 services, such as Microsoft Teams.
Note: You can customize the guest access settings based on your organization's external collaboration requirements.
5. Restrict access to Microsoft Entra administration portal- Setting this option to No allows non-administrators to browse the Microsoft Entra administration portal.
- Setting it to Yes restricts non-administrators from accessing the portal. Non-administrators who are group or application owners won’t be able to use the Entra ID portal to manage their resources.
- This setting does not restrict access to Microsoft Entra data via PowerShell, Microsoft Graph API, or other tools like Visual Studio. It also does not apply to users who are assigned custom or specific roles.
- Use this setting to prevent users from accidentally misconfiguring resources they own, but not as a security measure. For security, create a Conditional Access policy targeting the Windows Azure Service Management API to block non-administrators' access.
- To grant portal access to specific non-administrator users: Set this option to Yes, then assign the Global Reader role or another role to grant access to the portal.
The KMSI prompt is intentionally not shown in the following scenarios:
- The user signs in via seamless SSO with integrated Windows authentication (IWA).
- The user signs in via Active Directory Federation Services with IWA.
- The user is a guest in the tenant.
- The user has a high-risk score.
- The sign-in occurs during the user or admin consent flow.
- Persistent browser session control is enforced via a Conditional Access policy.
Entra ID Device Settings
- Cloud Device Administrator: Full access (read and modify)
- Intune Administrator: Read-only access
- Windows 365 Administrator: Read-only access
Configure this setting to let users register personal Windows 10 or newer, iOS, Android, and macOS devices. If set to "None," device registration is not allowed. Microsoft Intune or mobile device management requires registration, so if these services are configured, "All" is selected and "None" becomes unavailable.
This setting lets you specify the maximum number of Microsoft Entra joined or registered devices a user can have. The default is 50, and you can increase it up to 100 ,Configure unlimited for more than 100 devices. If users reach this limit, they must remove existing devices to add more. This setting doesn’t apply to hybrid joined devices.
This setting determines if the Global Administrator role is added to the local administrators group during the device’s registration as Microsoft Entra joined.
This setting adds the user registering the device as a local administrator during Microsoft Entra join.
Specify which users are granted local admin rights by adding them to the Device Administrators role in Microsoft Entra ID.
Enable Microsoft Entra Local Administrator Password Solution (LAPS) (preview):
LAPS manages local admin passwords on Windows devices, providing secure password storage and rotation for both Microsoft Entra joined and hybrid joined devices.
Admins can block non-admin users from accessing their BitLocker recovery keys. Default users without BitLocker read permission won’t be able to view or copy their keys. A Privileged Role Administrator is required to update this setting.
Entra ID Application Consent and Permissions Settings
Identity Protection Settings
This configuration offers two key benefits:
- Self-remediation for risky hybrid users: Hybrid users can resolve their own risks without administrator intervention. When a password is changed on-premises, the user's risk is automatically remediated within Microsoft Entra ID Protection, resetting their risk state.
- Proactive user risk policies: Organizations can enforce user risk policies that require password changes, providing stronger protection for hybrid users. This improves security and simplifies management by addressing user risks promptly, even in complex hybrid environments.
Note: Allowing on-premises password changes to reset user risk is an opt-in feature. Organizations should evaluate its impact before enabling it in production. Microsoft recommend securing the on-premises password change process, such as requiring multifactor authentication, by using tools like Microsoft Identity Manager's Self-Service Password Reset Portal.
The screenshot below displays the Identity Protection settings, which can be customized to align with your organization's specific business requirements.
Entra ID Conditional Access Policies
Microsoft has enhanced the Conditional Access policy experience by introducing an updated Overview and Coverage section, along with a new Monitoring tab for improved visibility.
- The Overview page provides a summary of policy status, users, devices, and applications, as well as general and security alerts with actionable recommendations.

- The Coverage page offers insights into applications that are and aren’t protected by Conditional Access policies over the past seven days.

- The Monitoring page enables administrators to view sign-in activity graphs, helping identify potential gaps in policy coverage with easy-to-use filters.
Entra ID Authentication Method Policies
Use authentication methods policies to define which authentication methods your users can register and use. If a user is within the scope for a particular method, they may use it for both authentication and password reset. Microsoft Entra multifactor authentication (MFA) adds an extra layer of security beyond a password by prompting users for additional verification, such as a push notification, a code from a software or hardware token, or a text or phone call response.
Some methods, like FIDO2 security keys or passwords, can be used as the primary sign-in factor for applications or devices, while others are only available as secondary factors during MFA or self-service password reset (SSPR).
Microsoft recommends passwordless authentication methods, including Windows Hello, Passkeys (FIDO2), and the Microsoft Authenticator app, for the most secure sign-in experience. While users can sign in with a username and password, it’s best to transition to more secure authentication options to reduce reliance on passwords.
| Method | Primary Authentication | Secondary Authentication |
|---|---|---|
| Windows Hello for Business | Yes | MFA* |
| Microsoft Authenticator push | No | MFA and SSPR |
| Microsoft Authenticator passwordless | Yes | No* |
| Microsoft Authenticator passkey (preview) | Yes | MFA and SSPR |
| Authenticator Lite | No | MFA |
| Passkey (FIDO2) | Yes | MFA |
| Certificate-based authentication | Yes | MFA |
| OATH hardware tokens (preview) | No | MFA and SSPR |
| OATH software tokens | No | MFA and SSPR |
| External authentication methods (preview) | No | MFA |
| Temporary Access Pass (TAP) | Yes | MFA |
| SMS | Yes | MFA and SSPR |
| Voice call | No | MFA and SSPR |
| Password | Yes | No |
*Windows Hello for Business alone does not act as a step-up MFA credential. For instance, it does not fulfill an MFA challenge from Sign-in Frequency policies or a SAML request with forceAuthn=true. However, it can be used as a step-up MFA credential when combined with FIDO2 authentication, which requires users to be registered for FIDO2.
* Passwordless sign-in can be used as a secondary authentication method only if certificate-based authentication (CBA) is used as the primary authentication.
Security questions & email address verification options – used exclusively for self-service password reset (SSPR)
Note: In Microsoft Entra ID, a password is typically a primary authentication method, and it cannot be disabled. To enhance security, you can add Microsoft Entra multifactor authentication when a password is used as the primary factor.
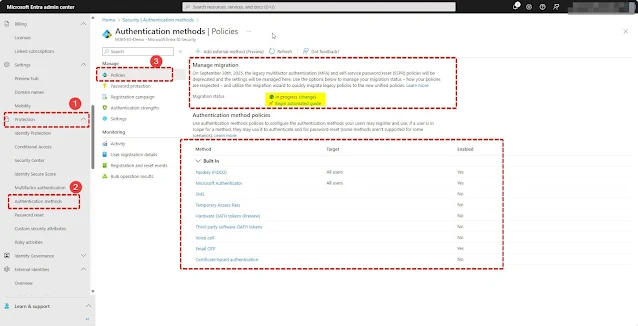
To review settings in the Authentication methods policy, sign in to the Microsoft Entra admin center as an Authentication Policy Administrator and go to Protection > Authentication methods > Policies.
By default, new tenants have all methods set to "Off." If you’re using legacy Per-user MFA and SSPR policies, a migration option is available in the new Authentication methods policy to unify MFA and SSPR settings. You need to click on Begin Automated guideRefer to the screenshot below for available SSPR authentication methods.
You can explore the updated UX for Legacy MFA settings by navigating to Entra Portal > All Users > Per-user MFA section.
The migration guide (preview) in the Microsoft Entra admin center provides an automated way to transition settings. This wizard audits current MFA and SSPR policies and consolidates them into the Authentication methods policy for easier, unified management. Alternatively, you can migrate settings manually at your own pace, and the process is reversible. The wizard lets you migrate with just a few clicks, starting from Protection > Authentication methods > Policies.
we need to select Next to Proceed with migrationDuring migration, the wizard will apply existing settings from legacy MFA and SSPR policies, with recommendations to also enable modern methods like passkeys, Temporary Access Pass, and Microsoft Authenticator to enhance security. Adjust configurations as needed using the pencil icon, and once satisfied, select Migrate to confirm. Legacy MFA and SSPR settings will then become inactive, and the migration status will update to Migration Complete. You can revert to In Progress anytime if needed to re-enable legacy settings.Note: A control for security questions will be available soon. If you currently use security questions and wish to keep them enabled, ensure they remain active in the legacy SSPR policy until the new control is released. You can complete the migration as outlined above, keeping security questions enabled.
You can refer to my previous blog post for details on the following authentication methods and their deployment steps:
Entra ID Password Protection
Smart Lockout
"Your account is temporarily locked to prevent unauthorized use. Try again later, and if you still have trouble, contact your admin."
During testing, sign-in requests may be routed through different data centers due to the geo-distributed, load-balanced nature of the Microsoft Entra authentication service.
Smart Lockout also tracks the last three failed password attempts, preventing the lockout counter from incrementing when the same incorrect password is repeatedly entered. In addition to Smart Lockout, Microsoft Entra ID further protects against attacks by analyzing IP traffic and identifying unusual behavior.
Custom Banned Password List
- Global banned password list: Microsoft Entra ID Free
- Custom banned password list: Microsoft Entra ID P1 or P2
- Global banned password list: Microsoft Entra ID P1 or P2
- Custom banned password list: Microsoft Entra ID P1 or P2
- Global Banned Password List: Automatically applied to all users in a Microsoft Entra tenant, this list includes commonly used weak or compromised passwords identified by Microsoft's security telemetry. This list is maintained by analyzing password trends and does not rely on third-party data. The global list is enforced automatically for all users during password changes or resets and cannot be disabled.
- Custom Banned Password List: To enhance security, organizations can add up to 1,000 custom terms, such as brand names, product names, or location-based terms unique to their company. This custom list combines with the global list to prevent the use of weak passwords during password updates. For maximum efficiency, it’s best to evaluate potential weak terms before adding them to the custom list.
- The list can hold up to 1,000 terms.
- Entries are case-insensitive and detect common substitutions (e.g., "o" and "0", "a" and "@").
- Each term must be between 4 and 16 characters.
To activate the custom banned passwords and save your entries, click Save.
Extending Protection to On-Premises AD DS
For hybrid identity environments with on-premises Active Directory (AD DS), organizations can extend the protection of Microsoft Entra Password Protection by deploying agents on-premises. These agents enforce the same password standards in AD DS, ensuring consistent security across both cloud and on-premises environments.
Note: On-premises AD DS users not synchronized to Microsoft Entra ID also benefit from Microsoft Entra Password Protection based on existing licensing for synchronized users.
We'll explore this configuration in depth in an upcoming blog series.
Additional Security Layers
To further secure user accounts, it’s recommended to combine password protection with Microsoft Entra multifactor authentication (MFA), rather than relying on strong passwords alone.
Microsoft Authenticator Registration Campaign
With a registration campaign, you can encourage users to set up the Microsoft Authenticator during their sign-in. After users complete their usual sign-in and MFA process, they’re prompted to set up the Authenticator app. You can target specific users or groups to nudge them from less secure authentication methods to Microsoft Authenticator.
Key Features:
- Snooze Option: Set how many days users can "snooze" the setup prompt. After choosing Skip for now, users will be reminded again during their next MFA attempt after the snooze period. You can allow indefinite snoozing or limit it to three times, after which registration is mandatory.
- Conditional Access Policies: Conditional Access rules for security info updates apply before prompting users to set up Authenticator. For example, if policies restrict security info changes to internal networks, users will only see the prompt when on that network.
Prerequisites:
- Microsoft Entra MFA Enabled: MFA must be enabled for your organization. Microsoft Entra ID includes MFA in all editions, so no additional licenses are required.
- Authenticator Not Already Set Up: Users should not have already set up push notifications in the Authenticator app.
- Enable Users for Authenticator: Admins should enable users for Authenticator via:
- MFA Registration Policy: Enable Notification through mobile app.
- Authentication Methods Policy: Set Authenticator app with Any or Push mode. (If set to Passwordless, users won’t receive a nudge prompt.)
Steps to Enable the Registration Campaign
- Sign in to the Microsoft Entra admin center as an Authentication Policy Administrator.
- Navigate to Protection > Authentication methods > Registration campaign, and select Edit.
- State Options:
- Enabled: Enable the campaign for all users.
- Microsoft Managed: Enable only for users using voice call or text messages for MFA. Microsoft manages default values.
- Snooze Configuration:
- Limited number of snoozes: Set to Enabled to limit to 3 snoozes, after which registration is mandatory. Set to Disabled for unlimited snoozes.
- Days allowed to snooze: Set the interval between prompts (e.g., 4 days).
- Exclude Users or Groups: Select any users or groups to exclude from the campaign, then click Save.
Additional Notes:
- The nudge prompt doesn’t appear on Android or iOS mobile devices.
- It only appears in embedded browser views within supported apps, not in out-of-the-box or embedded Windows settings experiences.
- Campaigns can run indefinitely; disable it through the admin center or APIs when ready.
- Nudges apply only if users are using Microsoft Entra’s multifactor authentication service.
- Nudges won’t appear if users encounter the Register security information block in Conditional Access, the Terms of Use (ToU) screen, or are redirected by custom Conditional Access controls.
Configuring Microsoft Entra Multifactor Authentication Settings
To customize the user experience for Microsoft Entra MFA, you can set options like account lockout thresholds, fraud alerts, and notifications. The Report suspicious activity feature replaces the legacy Block/unblock users, Fraud alert, and Notifications functions, which will be removed on March 1, 2025.
Report Suspicious Activity
The Report suspicious activity feature allows users to report unexpected or suspicious MFA prompts through the Microsoft Authenticator app or by phone. Alerts are integrated with Microsoft Entra ID Protection, adding advanced threat detection.
- High User Risk: When a suspicious prompt is reported, the user is marked as high risk. Administrators can then use risk-based policies to limit access or enable self-service password reset (SSPR) for user-initiated remediation.
- Non-P2 License Option: If you don’t have a Microsoft Entra ID P2 license, use risk detection events to manually identify and disable affected users or automate this process using custom workflows with Microsoft Graph.
Enabling Report Suspicious Activity
To enable Report suspicious activity:
- Sign in to the Microsoft Entra admin center as an Authentication Policy Administrator.
- Go to Protection > Authentication methods > Settings.
- Set Report suspicious activity to Enabled. (Choosing Microsoft managed keeps the feature disabled. For details on Microsoft-managed settings, see [Protecting authentication methods in Microsoft Entra ID])
- Choose All users or a specific group.
- If you’ve uploaded custom greetings for your tenant, select a Reporting code that users will enter to report suspicious activity. By default, the code is set to 0 unless custom greetings are uploaded.
- Click Save.
Note: If both Report suspicious activity and a custom voice reporting number are enabled, this feature will override any settings from the legacy Fraud Alert feature.
System-Preferred Multifactor Authentication (MFA)
System-preferred MFA prompts users to sign in using the most secure method they’ve registered, prioritizing security and minimizing reliance on less secure methods like SMS.
- Functionality: If a user has both SMS and Microsoft Authenticator push notifications set up, system-preferred MFA prompts them to sign in with the more secure push notification method. Users may still choose other methods but are encouraged to use the most secure option.
- Configuration: This is a Microsoft-managed, tristate setting that defaults to Enabled. You can change the setting to Disabled or exclude specific users and groups from the policy if you prefer not to enforce it.
- User Convenience: With system-preferred MFA enabled, the system automatically selects the most secure registered method for users, so they don’t need to set a default method manually.
- Sign in to the Microsoft Entra admin center as an Authentication Policy Administrator.
- Navigate to Protection > Authentication methods > Settings.
- Under System-preferred multifactor authentication, choose to explicitly enable or disable the feature.
- Include or exclude specific users or groups as needed, with exclusions taking precedence over inclusions.
By setting up system-preferred MFA, you enhance security by encouraging users to adopt their most secure authentication method.
Microsoft Entra External Collaboration Settings
External collaboration settings in Microsoft Entra allow you to manage who can invite external users for B2B collaboration, specify allowed or blocked domains, and control what guest users can see in your directory. Here’s an overview of the available options:
Key Options
- Guest User Access Control: Limit what external guest users can view within your directory, such as group memberships or only their profile.
Invite Permissions:
- Control who can invite external users. By default, all users can send invitations, but you can restrict this to specific roles.
Guest Self-Service Sign-Up via User Flows:
- Create user flows for applications to allow guest self-sign-up. This lets guests create accounts and register for apps within defined sign-up flows, specifying identity providers and attributes to collect.
Domain Restrictions:
- Specify which domains can or cannot receive invitations. For cross-tenant sign-ins, the home tenant’s branding appears if custom branding isn’t configured.
Configuring Guest Access
Sign in to the Microsoft Entra admin center as a Privileged Role Administrator.Navigate to External Identities > External collaboration settings.
- Anyone in the organization can invite guests (most inclusive).
- Member users and specific admin roles can invite guests.
- Only specific admin roles (e.g., User Administrator or Guest Inviter) can invite guests.
- No one can invite guests (most restrictive).
To enable self-service sign-up for applications, set Enable guest self-service sign-up via user flows to Yes. Create user flows to allow guests to sign up with selected identity providers and custom attributes.
The screenshot below shows the most optimal settings. You can adjust these settings to fit your business requirements.
External User Leave Settings:- Set Yes to allow external users to leave the organization independently.
- Set No to require admin approval for user removal requests.
- Add a privacy contact and a privacy statement to your Entra tenant to enable the external user leave settings. Microsoft recommend consulting legal advice to tailor privacy statements.
Configuring Collaboration Restrictions (Allow/Block Domains)
Under Collaboration restrictions, decide to allow or block specific domains.Enter domain names in the text boxes, placing each domain on a new line for multiple entries.
Important: Limit permissions by assigning roles with minimal necessary access for security. Global Administrator is highly privileged and should be used only in emergency scenarios.
Conclusion
Implementing the right security settings in Microsoft Entra ID is essential for safeguarding your organization’s resources while ensuring a seamless user experience. By following these recommended configurations, M365 Admins can strike a balance between robust security measures and usability, enhancing protection across identities, devices, and applications. Remember, these settings can be tailored to meet your specific business needs, so review them regularly and adjust as your organization evolves. With proactive management and a focus on best practices, you can leverage Microsoft Entra ID to build a secure, resilient identity infrastructure for your organization.






































0 Comments